Memory buffer overflow with Python
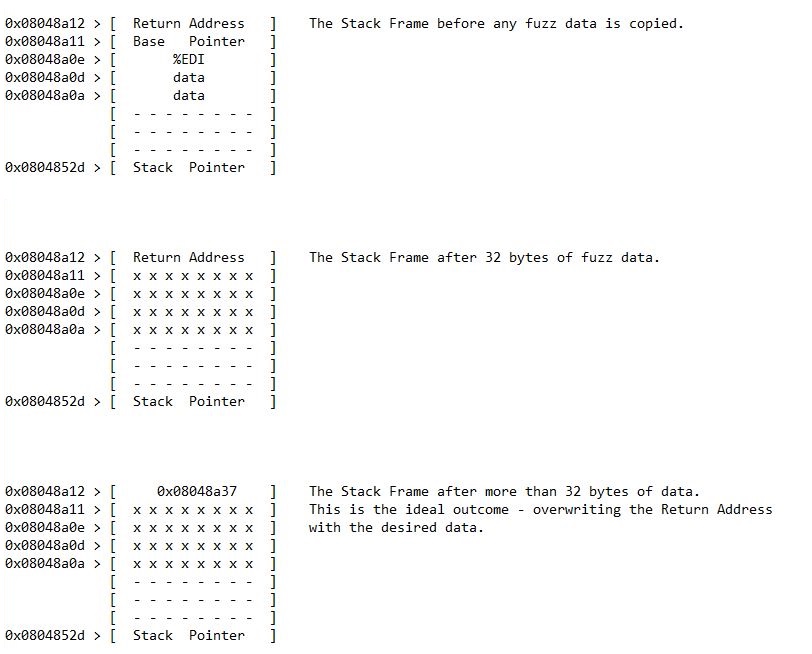
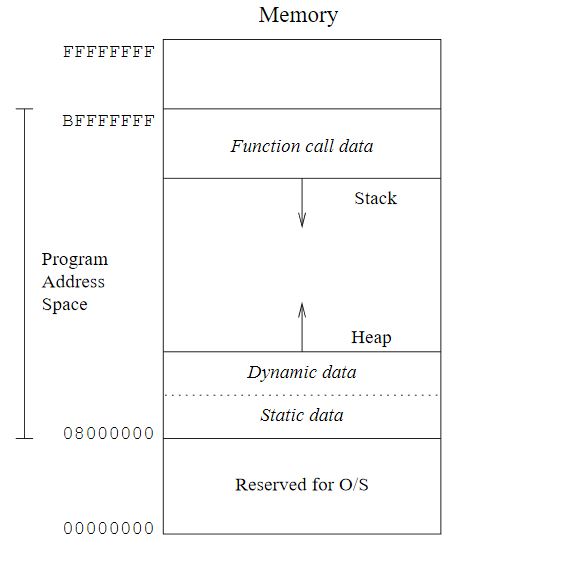
In a previous post, 'Memory and Stack Frames', I covered the basics of computer memory and stack frames. Now it's time to take that theory and give it a practical application. Under the spotlight is a C program that was presented as a flag in 'The Necromancer', a CTF challenge machine I downloaded from https://www.vulnhub.com/ . The file is named 'talisman' and presents the following output when it is run: You have found a talisman. The talisman is cold to the touch, and has no words or symbols on it's surface. Do you want to wear the talisman? The program is waiting for user input at this stage. After spending some time trying various words (' yes ',' no ',' maybe ',' wear ') and phrases (' wear the talisman ',' wear talisman ') it was clear that the answer was always the same - " Nothing happens. ". You have found a talisman. The talisman is cold to the touch, and has