Exploiting OpenSSH 4.7 / OpenSSL 0.9.8 (Metasploitable 2)
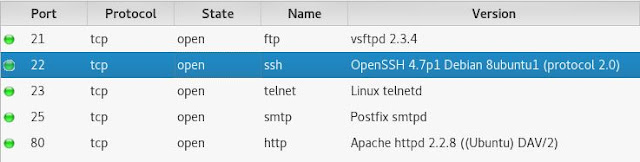
Metasploitable 2 is a deliberately vulnerable machine designed by Rapid 7, the company behind the immensely powerful and popular Metasploit Project. The machine is intended to be used for general security training and target practice; a perfect way to spend a lazy Sunday! The focus for this particular post will be the OpenSSH 4.7 protocol used by the vulnerable machine. This version of OpenSSH is several years old now, but the lessons learned here are still transferable to other services and newer versions. Before diving into the exploit it is necessary to understand the protocol being attacked and why it was vulnerable in the first place. OpenSSH is the freely available, open-source version of the SSH protocol. SSH itself is a cryptographic network protocol used to connect with network services securely over an un-trusted network. In plain English this means SSH is a secure way to login to servers and embedded devices that support the SSH protocol. While SSH has other uses...