Memory and Stack Frames
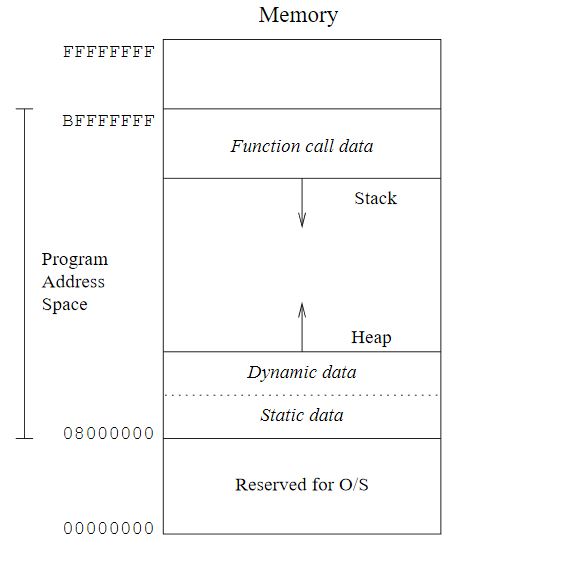
Recently I completed a Capture The Flag machine named 'The Necromancer' from the site VulnHub. If you've never heard of VulnHub before, it is essentially a site that provides 'hands-on' experience in digital security by way of virtual machines designed to be deliberately vulnerable to certain exploits ( https://www.vulnhub.com/about/ ). One of 'The Necromancer''s 11 flags requires the use of a memory buffer overflow. In short, a memory buffer overflow occurs when a program attempts to put more data into an allocated section of memory than it can hold (for instance, 50 bytes of data into a 40 byte memory buffer) causing the program to crash or, in some instances, execute malicious code. To understand and execute a memory buffer overflow first requires knowledge of memory, how it is allocated and how it is used. This knowledge is crucial to have before writing any code to execute an attack. In typical fashion I ended up with dozens of pages containing