Attacking wireless networks
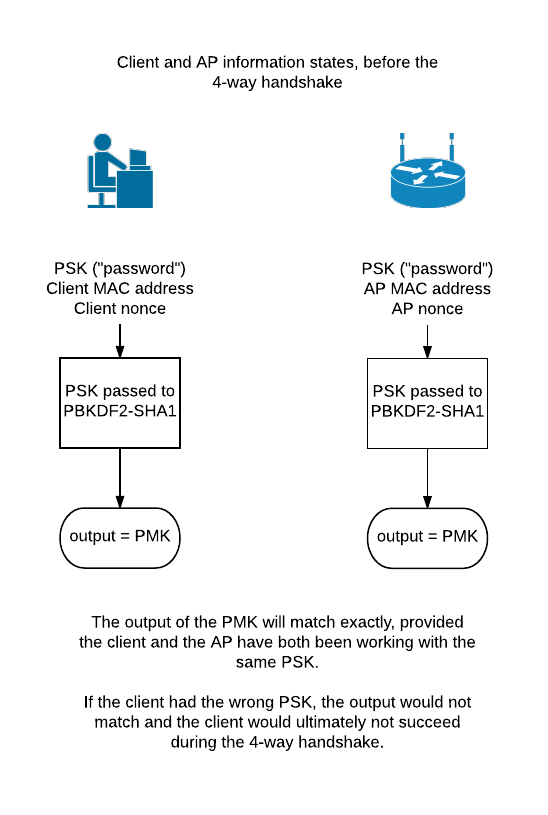
This post will be discussing the process by which a Client authenticates to a wireless network, and a common attack that is used to gain un-authorised access to wireless networks. There will be acronyms abound! When a Client joins a wireless network, it does so by means of a 4-way handshake designed to prove knowledge of the correct password (key) for that network. The key itself is "Pre-Shared", meaning both the Client and the Access Point have knowledge of the key prior to the handshake. The password, referred to as a 'Pre-Shared Key (PSK)', is never transmitted during the communication between the Client and the Access Point (AP). So, how then, does one obtain the password to such a network? Before obtaining the password it is first necessary to understand the measures taken to protect it. The Client and Access Point have knowledge of the Pre-Shared Key prior to the 4-way handshake. To be more specific - the Access Point is configured with the Pre-Sha