Encrypting traffic with IPsec protected GRE tunnel
Let's take a look at some options available to us when securing traffic that is transmitted over the Internet. For the sake of a scenario to work with lets consider that site A is an existing site with a 3rd party network we must integrate with, and site B is a newly commissioned site that now needs to receive traffic.
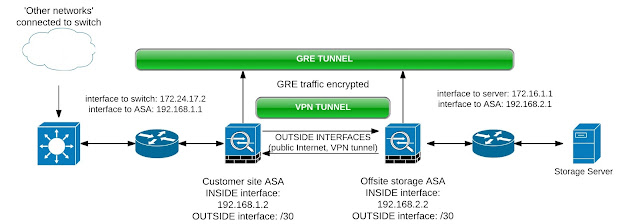
The deployment initially consists of two Cisco ASA 5505X's, each with a connection to a public Internet connection. A VPN is configured between these two devices to allow secure transmission of traffic from the third party network over the Internet to the storage server.
Worth mentioning is the basic configuration of a Cisco ASA. Out of the box it will require configuration for an 'Inside' and 'Outside' interface, as well as SSH for remote management:
## Cisco ASA interface configuration:
interface GigabitEthernet1/1 nameif outside security-level 0 ip address (publicIP) 255.255.255.252 interface GigabitEthernet1/3 nameif inside security-level 100 ip address 192.168.2.2 255.255.255.252
mtu outside 1500 mtu inside 1500
## Cisco ASA SSH configuration:
## The 'ssh 0.0.0.0 0.0.0.0 line' can be made more secure by listing
## a specific IP address that is allowed to use SSH for management.
aaa authentication ssh console LOCAL
ssh 0.0.0.0 0.0.0.0 outside ssh timeout 5 ssh version 2
username (name here) password (password here) encrypted
Cisco ASA's are not too dissimilar in their configuration of VPN tunnels to a Cisco router, but they are just different enough to cause headaches. Let's take a quick look a Cisco ASA VPN template (lines starting with "##" are comments):
## Cisco ASA VPN lan to lan configuration template.
## First, configure the phase 1 (IKE) tunnel between the two devices.
## Settings must match on both sides.
crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha-256 group 5 lifetime 28800 tunnel-group (peers public IP) type ipsec-l2l tunnel-group (peers public IP) ipsec-attributes ikev1 pre-shared-key (pre-share key)
## Phase 2 configuration - IPsec tunnel.
## The transform-set defines the parameters for the IPsec tunnel.
## The access-list identifies 'interesting' traffic.
crypto ipsec ikev1 transform-set (setname) esp-aes esp-sha-hmac access-list (vpn accesslist name) extended permit ip (internal lan of ASA) 255.255.255.0 (peer public IP) 255.255.255.255 access-list (vpn accesslist name) extended permit ip (public IP of ASA) 255.255.255.255 (peers internal lan) 255.255.255.0
## Next, bind it all together with crypto map statements!
## The configuration for PFS is included here for the sake of being complete.
crypto map MAP 1 match address (vpn accesslist name) crypto map MAP 1 set peer (peers public IP) crypto map MAP 1 set ikev1 transform-set (setname) crypto map MAP 1 set pfs group5 ## this line is completely optional. if it's being used, it needs to be used on both sides of the tunnel. crypto map MAP interface outside ## Cisco ASA's must always be NAT'ing traffic. Always.
## This poses a problem as NAT'ing traffic is not what we want to achieve here,
## We want to encapsulate it in ESP instead. The solution is the following:
object network (object network name1) subnet (internal lan of ASA) 255.255.255.0 object network (object network name2) subnet (peers internal lan) 255.255.255.0 nat (inside,any) source static (object network name1) (object network name1) destination static (object network name2) (object network name2) no-proxy-arp ## IP routing configuration. route outside (peers internal lan) 255.255.255.0 (peers external IP)
It's not as scary as it looks - really!
After completing the initial deployment we discover that the 3rd party network is sending Multicast traffic as opposed to Unicast traffic. Multicast traffic is not routed over the Internet so the answer here is to encapsulate the traffic in a GRE tunnel, however, Cisco ASA's do not support termination of GRE tunnels.
The answer to this problem is to deploy two Cisco 800 series routers, one alongside each ASA. The Cisco routers will be configured to handle multicast-routing and the GRE tunnel while the ASA's handle the VPN.
Looking at one of the Cisco routers now:
## First, enable multicast-routing
ip multicast-routing
## Setup some interfaces on the Router
interface Vlan1 description TO SERVER ip address 172.16.1.1 255.255.255.0 ip pim sparse-mode interface Vlan2 description TO ASA ip address 192.168.2.1 255.255.255.252 ip pim sparse-mode
## Now set up the GRE tunnel
## The IP address on the tunnel can be anything you like.
## The destination address is the remote network, in this case 192.168.1.1.
interface Tunnel0 ip address 192.168.3.2 255.255.255.252 ip pim sparse-mode tunnel source Vlan2 tunnel destination 192.168.1.1
## IP routing and IP 'multicast route' commands.
ip mroute 192.168.3.1 255.255.255.255 Tunnel0 ip mroute 172.24.17.2 255.255.255.255 Tunnel0 ip mroute 172.24.17.0 255.255.255.0 Tunnel0 ip route 172.24.17.0 255.255.255.0 192.168.3.1
ip route 0.0.0.0 0.0.0.0 192.168.2.2
Worth noting is that the size of each packet is well beyond 1500 bytes. With all the additional packet headers and encryption added by the GRE and VPN tunnels, packet fragmentation is now a problem. I'll explore this problem in much more depth later as it really deserves a post of its own.


Comments
Post a Comment