Reverse engineering a simple C program part 2 : GDB
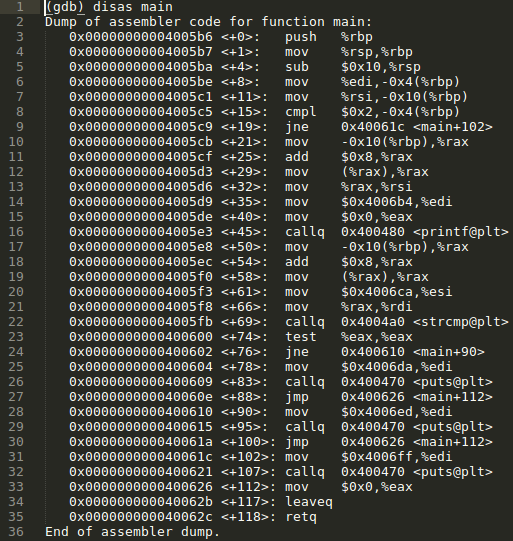
In part 1 of this simple reverse engineering exercise I examined a basic C program with 'Strings', 'Hexdump', and 'Ltrace'. These tools are useful for scratching the surface of a program with, but for in-depth analysis it is necessary to disassemble the program entirely. After loading GDB with the license crack program, setting a break point on main, running the program with no user input, and using the 'disassemble main' command, we are given the following output: The 'main' function This output is of the programs first and only function - 'main'. Every C program starts with a main function, and some may end within the main function while others may make calls to additional functions contained within the same code. The end goal here is to examine the programs functions until we draw a complete map of how the program executes. The focus will largely be on conditional instructions that influence flow control. Flow control is...